Learn STUN & TURN Servers on WebRTC
In our Introduction to WebRTC Module One, we covered the basics of STUN and TURN servers. This lesson will delve deeper into their functionalities, particularly highlighting their roles and strategies for effectively balancing STUN and TURN usage in WebRTC.
STUN (Session Traversal Utilities for NAT) and TURN (Traversal Using Relays around NAT) are foundational components in the WebRTC connectivity framework, ensuring seamless communication across even the most intricate network environments, including complex router configurations from end to end. To build a solid foundation, let's first revisit the concept of NAT (Network Address Translation) and explore the necessity for STUN and TURN to navigate these network complexities.
Understanding STUN
STUN, a protocol engineered to aid devices within a private network to identify their public IP addresses and the type of NAT they're behind, plays a pivotal role in navigating the vast expanse of router systems.
This system facilitates the discovery of each device's public address, a key factor in setting up peer-to-peer (P2P) communication sessions in WebRTC. Using a STUN server, two devices aiming to establish a connection can uncover their outward-facing IP addresses. This process allows them to circumvent NAT limitations, enabling a direct connection.
The figure below demonstrates the operation of STUN and the conditions under which a peer-to-peer connection is successfully established:
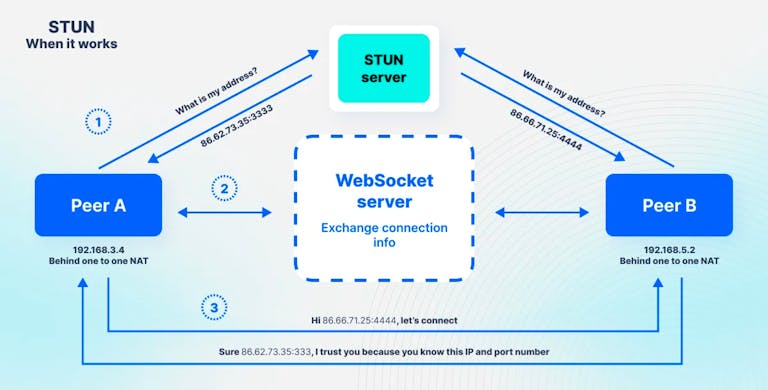
So, the primary attributes of STUN include the following:
- NAT Traversal: Facilitates devices in identifying their public IP addresses and NAT type, crucial for bypassing NAT-imposed connectivity hurdles.
- Simplicity and Efficiency: Offers an uncomplicated and effective method for enabling direct P2P connections, eliminating the need for significant infrastructure modifications.
When STUN Isn't Enough: TURN is a rescue
While STUN (Session Traversal Utilities for NAT) provides an efficient method for NAT traversal and establishing peer-to-peer connections in numerous cases, it faces significant challenges with stringent NAT setups or intricate firewall restrictions. TURN (Traversal Using Relays around NAT) servers become essential in such situations. Acting as intermediaries, TURN servers facilitate the relay of traffic between devices unable to form a direct connection.
Unlike STUN's objective of enabling direct connections, TURN guarantees communication across even the most restrictive network environments. For instance, when a peer is located behind a symmetric NAT—a router configuration that introduces added security and complexity in managing public and private network addresses—establishing a direct peer connection becomes notably difficult. TURN servers address this challenge by ensuring a reliable communication pathway, making them invaluable for consistent connectivity in complex network scenarios.
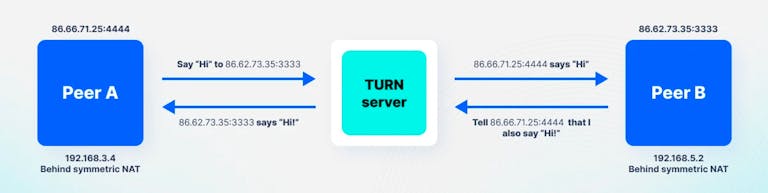
So, the benefits of employing TURN include:
- Reliability: TURN ensures consistent connectivity between peers by relaying traffic through a server, effectively bypassing NATs and firewalls.
- Universal Compatibility: TURN serves as a reliable backup in scenarios where STUN encounters limitations, facilitating the establishment of WebRTC connections even in challenging network conditions.
Best Practices for Building TURN and STUN Servers
Now you should have a better understanding of STUN and TURN servers. As explored, these protocols are pivotal in enhancing connectivity within WebRTC applications by adeptly navigating through NATs and firewalls, ensuring seamless communication channels.
So, constructing TURN and STUN servers demands a meticulous approach centered on enhancing reliability, fortifying security, and integrating robust fallback mechanisms. This section provides a comprehensive guide to the best practices for deploying TURN and STUN servers to optimize their efficiency and reliability.
Prioritizing Server Reliability
The strategic deployment and management of STUN and TURN servers are paramount in maintaining high server reliability for WebRTC services. Here are key practices to consider:
1. Optimize Server Deployment: Leveraging STUN and TURN servers across multiple geographic locations reduces latency and bolsters connection stability. This strategy of geographical diversification ensures that users can connect to the closest server, thereby diminishing the burden on any single server and boosting overall system reliability. This approach taps into the concept of a global edge network. Such a network spreads networking infrastructure worldwide, aiming to deliver content and services to users as proximally as possible, irrespective of their geographical positions. By storing WebRTC data (such as texts, videos, and images) on these edge servers, the global edge network facilitates serving this content from the nearest server rather than a central data center potentially located continents away. Consequently, the integration of an edge network not only optimizes server performance but also significantly enhances user experiences.
2. Intelligent Resource Scaling: TURN servers are prone to experiencing spikes in bandwidth consumption. Proactively monitoring server load and implementing dynamic resource scaling are essential measures to avert server overload and preserve the quality of service during periods of high demand. This strategic approach ensures that server capacity aligns with usage patterns, maintaining optimal performance even under heavy load.
3. Strengthen Security and Uphold Compliance: To fortify the defenses of STUN and TURN servers, it's imperative to update server software, addressing vulnerabilities promptly and consistently. Additionally, incorporating measures such as rate limiting and robust authentication protocols can protect against unauthorized access and potential abuse, thus preserving server integrity and performance. These proactive steps enhance security and ensure adherence to regulatory standards, safeguarding the infrastructure and user data.
4. Vigilant Monitoring and Agile Adaptation: The key to maintaining optimal server performance and user connectivity lies in the relentless monitoring of server operations and the proactive identification of connectivity challenges. By meticulously analyzing instances of failed connections, valuable insights can be gained regarding the need to deploy more TURN servers or tweak STUN server configurations to boost connection success rates. This approach ensures a smooth user experience and enables swift adaptation to evolving network demands and user expectations.
STUN and TURN are more than just tools for overcoming NAT and firewall restrictions. By strategically deploying these servers, scaling resources appropriately, ensuring security, and continuously monitoring performance, organizations can provide reliable, high-quality WebRTC services.
Ensuring Robust Security
WebRTC enables real-time audio, video, and data sharing directly within web browsers without additional plugins or applications. While this provides immense convenience and flexibility, it also opens up potential vulnerabilities that malicious actors could exploit. Ensuring robust security measures are in place is essential to protect both users and the integrity of the WebRTC ecosystem. Here are some best practices for enhancing WebRTC securities:
1. Regularly Update WebRTC Components: It's critical to consistently update all WebRTC components, libraries, and dependencies to address any potential vulnerabilities. Google actively maintains WebRTC, regularly addressing and patching known vulnerabilities to bolster WebRTC's security. Stay informed about the latest improvements and changes by monitoring the WebRTC repository, where updates and patches are routinely posted. This proactive approach is essential in maintaining the security integrity of your WebRTC applications.
2. Fortify with Application-Level Security Measures: While WebRTC provides a solid foundation of security features, layering additional application-level security practices is imperative. Implement robust authentication mechanisms, comprehensive authorization controls, and stringent input validation processes to safeguard against pervasive threats, including identity theft and session hijacking. These measures complement WebRTC’s built-in security and fortify your application's defense against sophisticated cyber-attacks, ensuring a secure and trusted user environment.
3. Strengthen Signaling Channel Security: Despite WebRTC's encryption of media streams, the protocol does not inherently define the signaling mechanisms for initiating and managing communication sessions. It's crucial to secure these signaling pathways, which frequently utilize WebSocket or HTTP, by implementing HTTPS (HyperText Transfer Protocol Secure) or WSS (WebSocket Secure). This ensures the integrity and confidentiality of the signaling data against eavesdropping and tampering, providing a fortified layer of security to the foundational communication channels of your WebRTC application.
4. Prioritize Continuous Security Evaluations: Consistently conducting security audits and penetration testing is vital for maintaining the integrity of your WebRTC application. These thorough evaluations assess the application's current security stance, identifying and rectifying vulnerabilities before they can be exploited. By proactively pinpointing and mitigating security weaknesses, you can avert potential security breaches and ensure the ongoing protection of user data and application functionality. This proactive approach to security underscores a commitment to safeguarding your WebRTC environment against evolving cyber threats.
By utilizing the inherent security capabilities of WebRTC and implementing established best practices for application security, developers are equipped to construct communication platforms that are not only secure but also reliable. Moreover, this comprehensive approach to security plays a crucial role in protecting user information from potential hackers, a paramount consideration in providing secure services. This dual focus on leveraging WebRTC's security strengths while proactively defending against cyber threats ensures a trusted user environment.
Conclusion
You've explored the intricacies of TURN and STUN servers, along with best practices for their development. Establishing reliable and secure TURN and STUN servers is crucial for facilitating superior real-time communication experiences. Adhering to these best practices enables developers to construct a resilient infrastructure that underpins the flawless operation of WebRTC applications, ensuring seamless connectivity across the board.